Fake Browser Update Analysis - SmartApeSG
-
ZPHP/SmartApeSG is a malware campaign that uses fake browser updates on legitimate sites to trick users into downloading and installing a Remote Access Trojan (RAT).
-
It uses Net Support Manager software tool as a RAT, allowing remote control to adversaries.
- NetSupport Manager is a legitimate tool for remote desktop control.
Infection Process
- High level:
- User visits a compromise website.
- Website displays a message saying that the Browser’s version is out of date and must be updated.
- User clicks the button to download the update.
- User gets infected by RAT.
- A bit more detailed:
- User visits a compromised website (Stage 1 domain).
- This is a legitimate site that has been injected with malicious JavaScript.
- The malicious script makes an asynchronous request to a second domain (Stage 2).
- “/cdn/wds.min.php”.
- “/cdn-js/wds.min.php”.
- The Stage 2 server responds with heavily obfuscated JavaScript, which:
- Evaluates whether the visitor is a valid target (based on geolocation, browser, etc.).
- If yes, it creates a hidden <iframe> that requests:
- “/zwewmrqqgqnaww.php?reqtime=<epoch>”
- The server behind ““/zwewmrqqgqnaww.php” responds not with visible content in the iframe, but with JavaScript that is executed in the parent page context.
- The iframe loads a fake browser update prompt.
- This JavaScript replaces or overlays the page with the fake browser update with a prompt like: “Your browser is out of date. Please update now.”
- User clicks the “update” button.
- A malicious Base64 encoded ZIP file is downloaded, containing:
- A .js file (NetSupport RAT loader)
- A malicious Base64 encoded ZIP file is downloaded, containing:
- The malware executes and installs a payload.
- NetSupport Manager is silently installed as a Remote Access Trojan (RAT).
- Attacker gains persistent access to the system.
- (Don’t be so hard with my drawing):
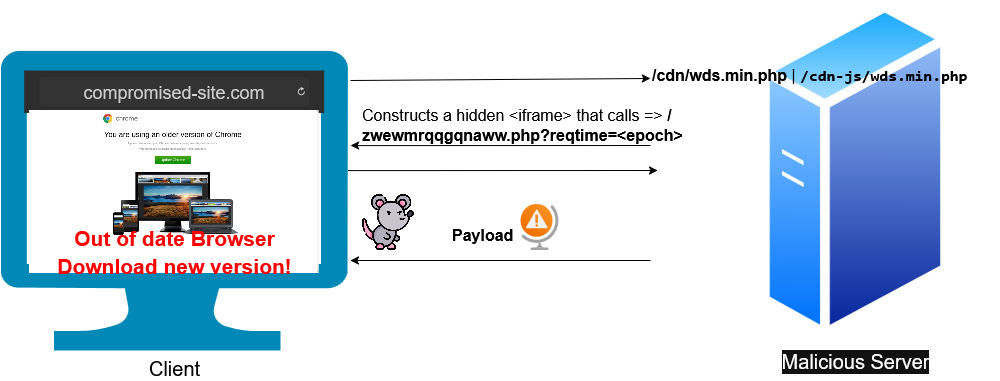
- Stage 1: A compromised legitimate website that has been injected with malicious JavaScript. This site is what the user visits unknowingly.
- Stage 2: A malicious or attacker-controlled server that receives traffic from Stage 1 and delivers additional JavaScript or the actual malware payload.
MITRE ATT&CK
- High level from the MITRE ATT&CK.
| Tactic | Technique | ID | Explanation |
|---|---|---|---|
| Initial Access | Drive-by Compromise | T1189 | User visits a legitimate but compromised website with malicious JS. |
| Execution | User Execution | T1204 | User manually executes a downloaded ZIP, JS, or EXE file. |
| Persistence | Registry Run Keys / Startup Folder | T1547 | RAT is configured to auto-start at system boot. |
| Defense Evasion | Obfuscated Files or Information | T1027 | JavaScript and payloads are obfuscated to evade detection. |
| Command and Control | Application Layer Protocol: Web Protocols | T1071 | NetSupport RAT communicate over HTTP/S. |
| Exfiltration (if present) | Exfiltration Over C2 Channel | T1041 | Exfiltration via the same C2 channel. |
Network Analysis
- This site “https://www.malware-traffic-analysis.net/2024/11/26/index.html” is doing a fantastic job for guys like me that want to analyze malware infections.
- In above link there is a pcap file that the author capture in a control environment and asks us to complete some tasks.
- Analyzing these traces must be done in the correct way. Read authors page!
- Given details:
- LAN segment range: 10.11.26[.]0/24 (10.11.26[.]0 through 10.11.26[.]255)
- Domain: nemotodes[.]health
- Active Directory (AD) domain controller: 10.11.26[.]3 - NEMOTODES-DC
- AD environment name: NEMOTODES
- LAN segment gateway: 10.11.26[.]1
- LAN segment broadcast address: 10.11.26[.]255
- Task:
- Write an incident report based on malicious network activity from the pcap and from the alerts.
- The incident report should contains 3 sections:
- Executive Summary: State in simple, direct terms what happened (when, who, what).
- Victim Details: Details of the victim (hostname, IP address, MAC address, Windows user account name).
- Indicators of Compromise (IOCs): IP addresses, domains and URLs associated with the activity. SHA256 hashes if any malware binaries can be extracted from the pcap.
Interesting Alerts In The Given Files
- ET CURRENT_EVENTS ZPHP Domain in DNS Lookup (modandcrackedapk.com)
- 10.11.26.183 -> 10.11.26.3
- sport=52957 -> dport=53
- ET POLICY HTTP Request on Unusual Port Possibly Hostile
- 10.11.26.183 -> 194.180.191.64
- sport=53362 -> dport=443
- ET POLICY HTTP POST on unusual Port Possibly Hostile
- 10.11.26.183 -> 194.180.191.64
- sport=53362 -> dport=443
- ETPRO TROJAN NetSupport RAT CnC Activity
- 10.11.26.183 -> 194.180.191.64
- sport=53362 -> dport=443
- ET POLICY HTTP traffic on port 443 (POST)
- 10.11.26.183 -> 194.180.191.64
- sport=53362 -> dport=443
- These alerts are here because the IDS recognized these type of activities/traffic.
WireShark Analysis
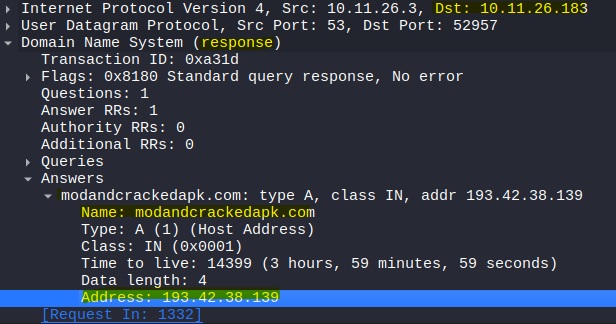
- Domain name “modandcrackedapk.com” is flagged as “ZPHP” in the alerts. Let’s find out to which IP address resolves to.
- From below image we can also find out who the victim likely is.
dns.qry.name eq modandcrackedapk.com
modandcrackedapk.com => 193.42.38.139
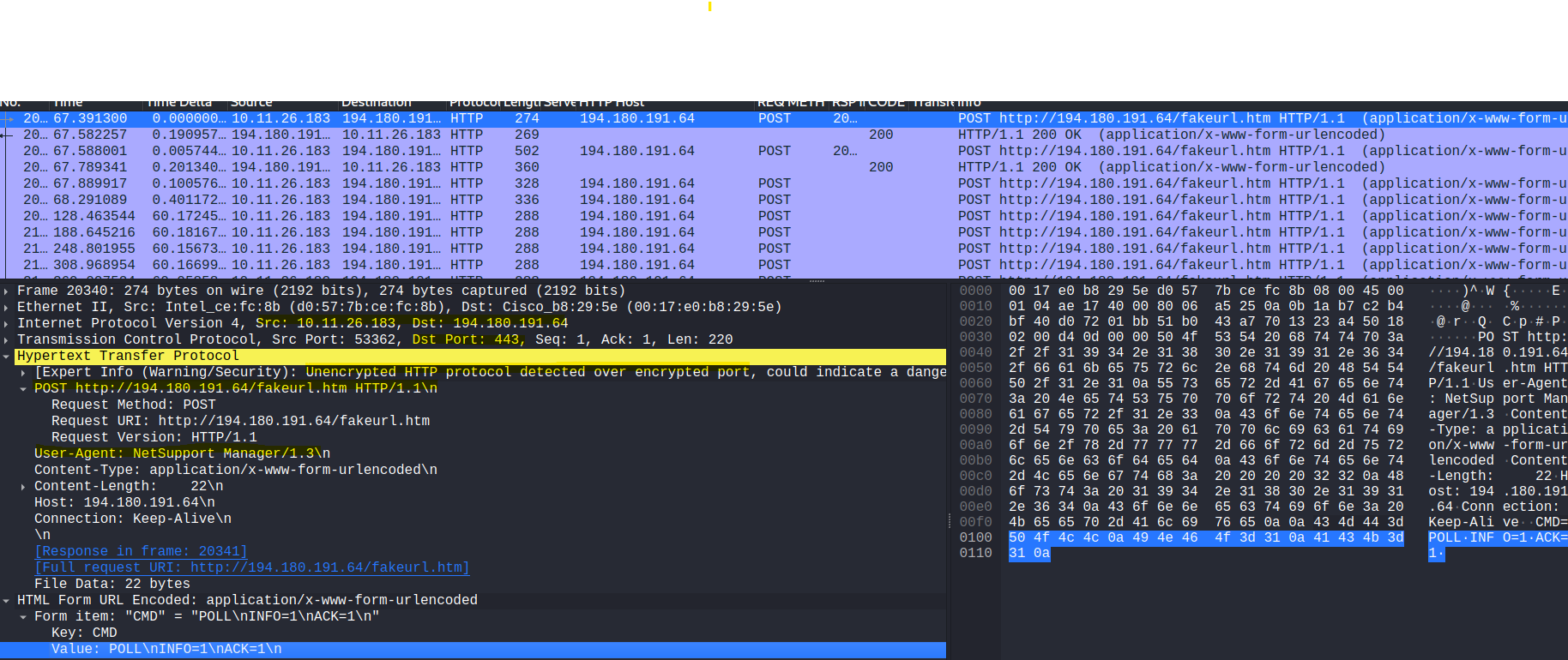
- The rest of the alerts involves the same addresses. What I can tell from below image:
- Victim’s details:
- IP Address: 10.11.26.183
- MAC Address: d0:57:7b:ce:fc:8b
- This is HTTP traffic, but the destination port is 443. In general, you can use any port for whatever traffic you want. Just as you can have an HTTP site over port 80, you can also use port 8080. So, yes you can use port 443 for HTTP traffic, but this will definitely attract some attention. Standard port for HTTPS traffic is 443, period, you just don’t use it for anything else; you may publish your HTTPS site on another port, but you would not use port 443 for another purpose other than HTTPS (at least I don’t see any other use for this port, otherwise it will just cause confusion).This is very odd and probably it was used to disguise the packets. Even WireShark alerts us to pay attention to this.
- Client is POSTing data to a server.
- The User-Agent is the NetSupport Manager that got installed, acting as a RAT. If your organization does not use NetSupport Manager, this is a clear red flag.
- There are a bunch of messages between victim and C&C and they are exchanging lots of information.
- Hostile C&C IP Address: 194.180.191.64
- Victim’s details:
ip.addr eq 10.11.26.183 and ip.addr eq 194.180.191.64 and http
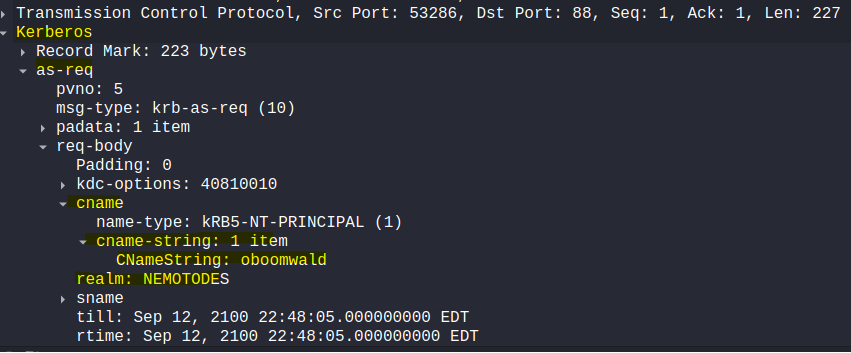
- To find out the Windows user account we can filter for Kerberos traffic and look for the Authentication Request (AS-REQ)
kerberos.as_req_element
- NEMOTODES\oboomwald
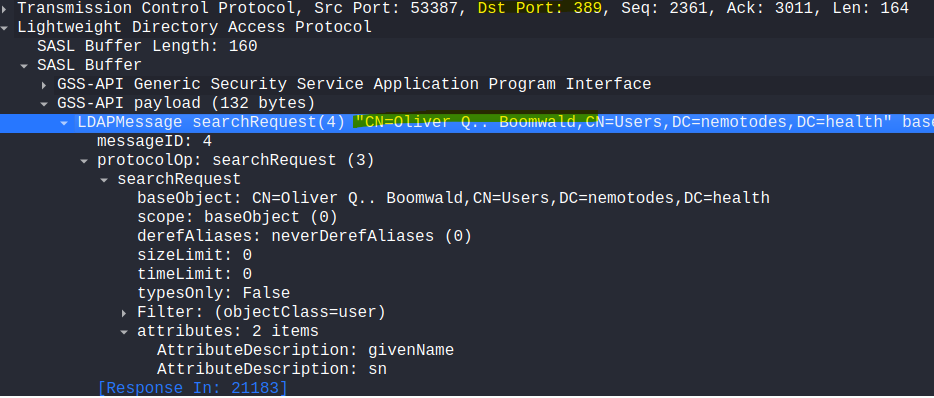
- To find out the actual name of the person we can find this in the LDAP protocol. In the pcap LDAP is being used instead of LDAPS, good for us. We can search for packets that contain common attributes like “givenName”.
- Oliver Q Boomwald
ldap.AttributeDescription eq givenName
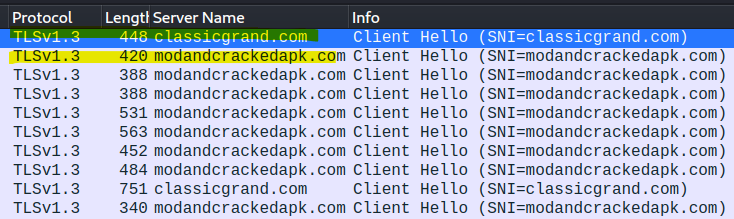
- As for how to find out which was likely the site that got compromised there is no way for me to objectively determine from within just the pcap. Maybe something I missed?? Sure, I see some funny domain names in the pcap, but I simply cannot conclude that “X” site was the site that got compromised.
- From outside research you may find that one of these site is/was “classicgrand.com” and that would be the answer for this exercise.
- Traffic to “modandcrackedapk.com” and “classicgrand.com” is using TLSv1.3. There is nothing for me to see there other than the IP Address and maybe some potentially interesting TLS extension, but feels more like a dead end.
tls.handshake.extensions_server_name == "modandcrackedapk.com" || tls.handshake.extensions_server_name == "classicgrand.com"
# or
tls.handshake.type eq 1 # For Client Hello
Incident Report
Executive Summary
- On 2024-11-26 around 04:50 UTC a Windows host from one of the NEMATODES domain employee got infected with NetSupport RAT after visiting a compromised site that led to downloading the malware from a stage 2 domain (likely modandcrackedapk.com).
Victim Details
- IP Address: 10.11.26.183
- MAC Address: d0:57:7b:ce:fc:8b
- Windows Account: NEMOTODES\oboomwald
- Name: Oliver Q Boomwald
Indicators of Compromise (IOCs)
- HTTP traffic over port 443.
- Multiple POST to a IP flagged as NetSupport traffic.
- POST http://194.180.191.64/fakeurl.htm
- ZPHP domain flagged.
- modandcrackedapk.com
Defenses:
- Train users to avoid browser update and in general, promote a “don’t click blindly” culture. Updates should always come from IT Administration.
- Use DNS filtering, this can help you blocked known bad domain names. Attackers are always comming up with new domains, but it is worth using DNS filtering.
- Monitor hidden iframes to unkown URL?
- Deploy EDR solutions.
- Block remote management from tools that your organization does not use.
- Consider Application Allow Listing.
- Prevent ZIP execution in user directories.
- Block file downloads (.zip, .js, .exe) from unknown sources.
- Monitor and block for URL specific patterns like “/cdn/wds.min.php”,etc.
- IDS/IPS.