Introduction
- As part of my own training in malware analysis, today I decided to give it a try at the famous WannaCry Ransomware.
- My goal is to identify the fundamental parts of this malware and what it does when it is executed.
- Malware obtained from this amazing repo:
- There are several things I still need to get better at, but that won’t hold me for trying.
- If anyone has any kind of advice/tip/recommendation, please share!
Scenario
In the early summer of 2017, WannaCry was unleashed on the world. Widely considered to be one of the most devastating malware infections to date, WannaCry left a trail of destruction in its wake. WannaCry is a classic ransomware sample; more specifically, it is a ransomware cryptoworm, which means that it can encrypt individual hosts and had the capability to propagate through a network on its own.
Questions
- Record any observed symptoms of infection from initial detonation. What are the main symptoms of a WannaCry infection?
- Use FLOSS and extract the strings from the main WannaCry binary. Are there any strings of interest?
- Inspect the import address table for the main WannaCry binary. Are there any notable API imports?
- What conditions are necessary to get this sample to detonate?
- Network Indicators: Identify the network indicators of this malware
- Host-based Indicators: Identify the host-based indicators of this malware.
- Use Cutter to locate the killswitch mechanism in the decompiled code and explain how it functions.
Analysis
Static
- SHA256:
- 24d004a104d4d54034dbcffc2a4b19a11f39008a575aa614ea04703480b1022c
- VirusTotal:
- This is categorized as a trojan/ransomware/worm.

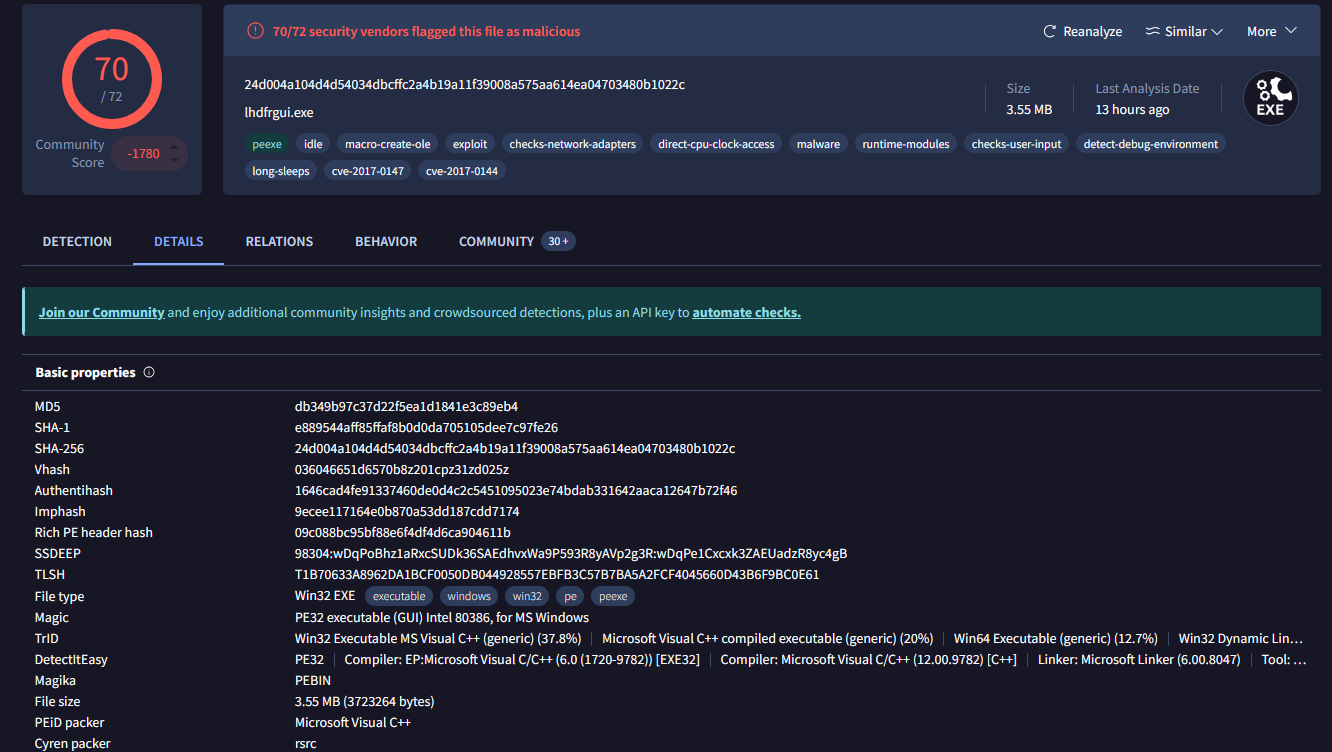
- Some of the strings I managed to find without looking too much into it:
- The string “tasksche.exe” is interesting because one may think we are talking about “Task Scheduler”, however its real name is “taskschd”. So, this is for sure interesting.
- “icacls.exe” is used to modify file/folder permissions and grand “Everyone” full access. Not sure yet where is this being used.
- /f: full control
- /t: Performs the operation on all specified files in the current directory and its subdirectories.
- /c: Continues the operation even if file errors occur. Error messages are still shown.
- /q: quite mode, no success messages
- URI: “[hxxp]://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com”
- Suspicious string of “C:\%s\qeriuwjhrf”. The “%s” gets substituted it at runtime.
- Some API’s related to possible HTTP calls.
- Several Base64 strings
- This string “!This program ….” tells us that there are other executables inside this malware.
!This program cannot be run in DOS mode.
!This program cannot be run in DOS mode.
!This program cannot be run in DOS mode.
!This program cannot be run in DOS mode.
C:\%s\qeriuwjhrf
tasksche.exe
[hxxp]://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com
icacls . /grant Everyone:F /T /C /Q
diskpart.exe
InternetOpenUrlA
InternetOpenA
WININET.dll
fd4d9L7LS8S9B/wrEIUITZWAQeOPEtmB9vuq8KgrAP3loQnkmQdvP0QF9j8CIF9EdmNK3KEnH2CBme0Xxbx/WOOCBCDPvvjJYvcvf95egcjZ+dWquiACPOkTFW3JS6M+sLa/pa6uVzjjWOIeBX+V3Pu12C9PjUWOoRfFOAX+SFzVJL4ugpzxsVRvgFvIgqXupq+y6bfWsK90pWeE5qzBSTKcSepm0GPGr/rJg0hJn4aVBbsdnXxM2ZCDorVUsFUsF9vXC2UIJlsx5yEdThqQ5MoEd6tRwRSfYA87dvMJrPfpB8qLIaFHNX684tJJn30Bx0vnkLW3oRcGKuBqZdJ/PI4yIm++QVKkBLVa106S2gpwejplTs510cW0VN+8yVJAuZhPZSij7FLlAE4zS0bjSo6lP098nSduB9h9eziOeLhd1KG16h+g8xP2CV1VsNhr9ao+2cmCeiHYhbceDilST+ASGztHMWarFIlJUL6qlCrptzEJTk+er2j7SfHHT0nNtEa4+JRvPq5C21Kd1pcQ7vKlvZ5flQs1vvXTGZhYZKTv5lrdWNEtVEzGh+KvTFJxqKz5LNvLPT/0yRqcO6deL/nmv3UCt+B0Ut2X6cNonJG76Ut78wcRv4YP2MwApDS9fSz2AGGVxm246qiUiKWWtM6w40aDjuPH7gCQEoDHwhJgvLgmSaibPwjJrDzO0hMGDrp6SxwIFNS1G2oAPcvOn4CL4JDuLCBs08NtDrQysl0WMgCIBM+1O5D8Lue0J0359/4fCzqNCvBoqgyss9YWZb6wy6C/Kz4ak/Qmt74uXsA71fduIs3zEs6CAPpQQlvXMlZYWczpenAS2b+gO6aHHEFZBJmJ6Vy9I4RoLIPH/8Ig1ManJzkgPODvGvcuE/WUDFmiIiwGMlFMFTchBTVUQSPaLFWMUk6FqeO1LTY2/Rc3lSWSuBVeAAtlUNa6kfXqh/9==
- Windows Portable Executable.
- 32-bit binary.
- Compiled 2010/11/20 Sat 09:03:08 UTC.

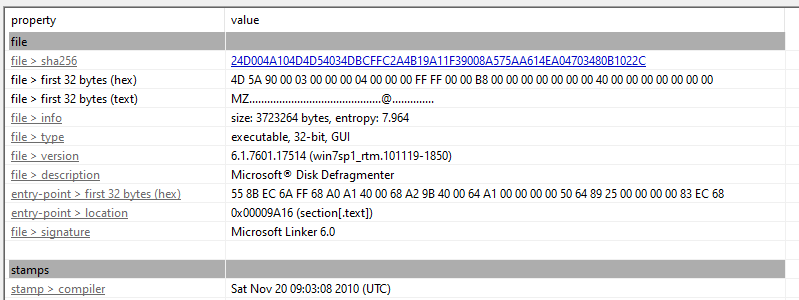
- Import Address Table (IAT): nothing definitive, however there are some interesting API’s that MIGHT be used malware developers:
- InternetOpenA: used to initialize the use of WinINet functions.
- InternetOpenUrlA: open a resource specified by a complete FTP of HTTP URL.
- GlobalAlloc: used to allocate the specified number of bytes from the heap.
- GetProcAddress: used to get the memory address of a function in a DLL. This is often used by malware for obfuscation and evasion purposes to avoid having to call the function directly.
- Sleep: used to suspend the execution of the current thread for a set time. This function is commonly used for time-based evasion by adding delays in the code.
- CryptGenRandom: CryptGenRandom is used to fill a buffer with cryptographically random bytes.
- CryptAcquireContextA: CryptAcquireContextA is used to acquire a handle to a particular key container within a particular cryptographic service provider (CSP).
- IsDebuggerPresent: used to determine whether the calling process is being debugged by a user-mode debugger. \
- VirtualAlloc: VirtualAlloc is often used by malware to allocate memory as part of process injection.
- VirtualProtect: used by malware to modify memory protection (often to allow write or execution).
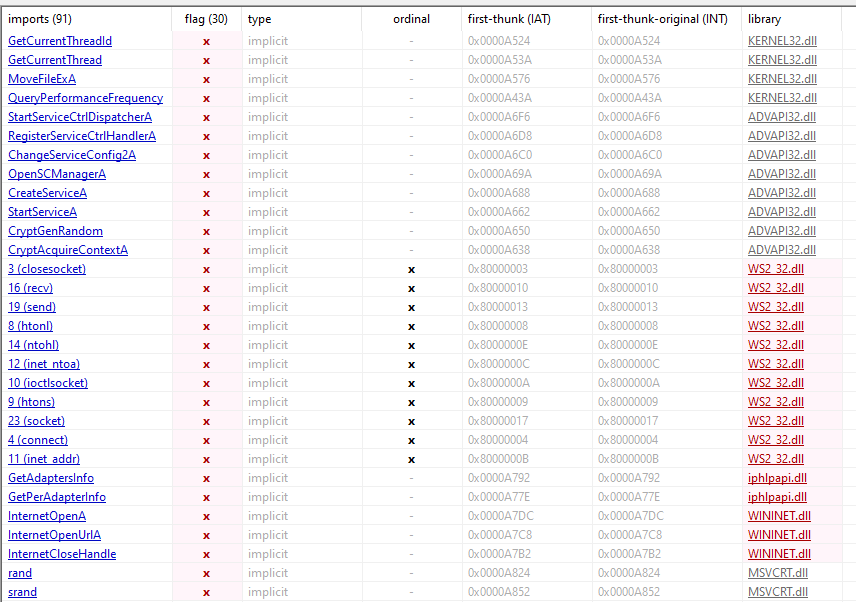
- Take a look at the following image:
- I am not that good at assembly, trying to get better. But here is my take:
- From the above image we can see it is preparing to make a call and then executing that HTTP call.
- InternetOpenA API This returns a valid handle that the application passes to subsequent WinINet functions. This is stored in register “eax”
- Then the handle is passed onto InternetOpenUrlA API along with that strange domain “[hxxp]://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com”. This returns a valid handle to the URL if the connection is successfully established, or NULL if the connection fails.
- These are the InternetOpenUrlA parameters:
- hInternet: The handle to the current Internet session.
- lpszUrl: the URL string.
- lpszHeaders: request headers.
- dwHeadersLength: the size of the additional headers
- dwFlags: several options (see doc).
- dwContext: a pointer to a variable that specifies the application-defined value that is passed, along with the returned handle, to any callback functions.
- These are the InternetOpenUrlA parameters:
- The result of calling InternetOpenUrlA is stored in register “eax”, which then it is moved into “edi”.
- Then we test the “edi” register against itself.
- The “test” instruction will update the “Zero Flag” (ZF), based on if the value of the register is zero (ZF == 1) or non-zero (ZF == 0).
- Assuming InternetOpenUrlA was successful, “edi” will have some kind of non-zero value and the “ZF” will have a value of “0”.
- Assuming InternetOpenUrlA failed, “edi” will have a NULL/zero value, then the “ZF” will have a value of “1”.
- Now, the “jne 0x4081bc” instruction will go either left or right path based on the value of “ZF”.
- If “ZF” == 0 (“edi” is non-zero, HTTP call was successful), then jump to that location in memory and exit out of the program.
- If “ZF” == 1(“edi” is zero, HTTP call failed), then continue as normal and execute payload.
- Basically this can be summarize in “If the call to ‘‘[hxxp]://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com’ failed, do this; otherwise exit out of the program.
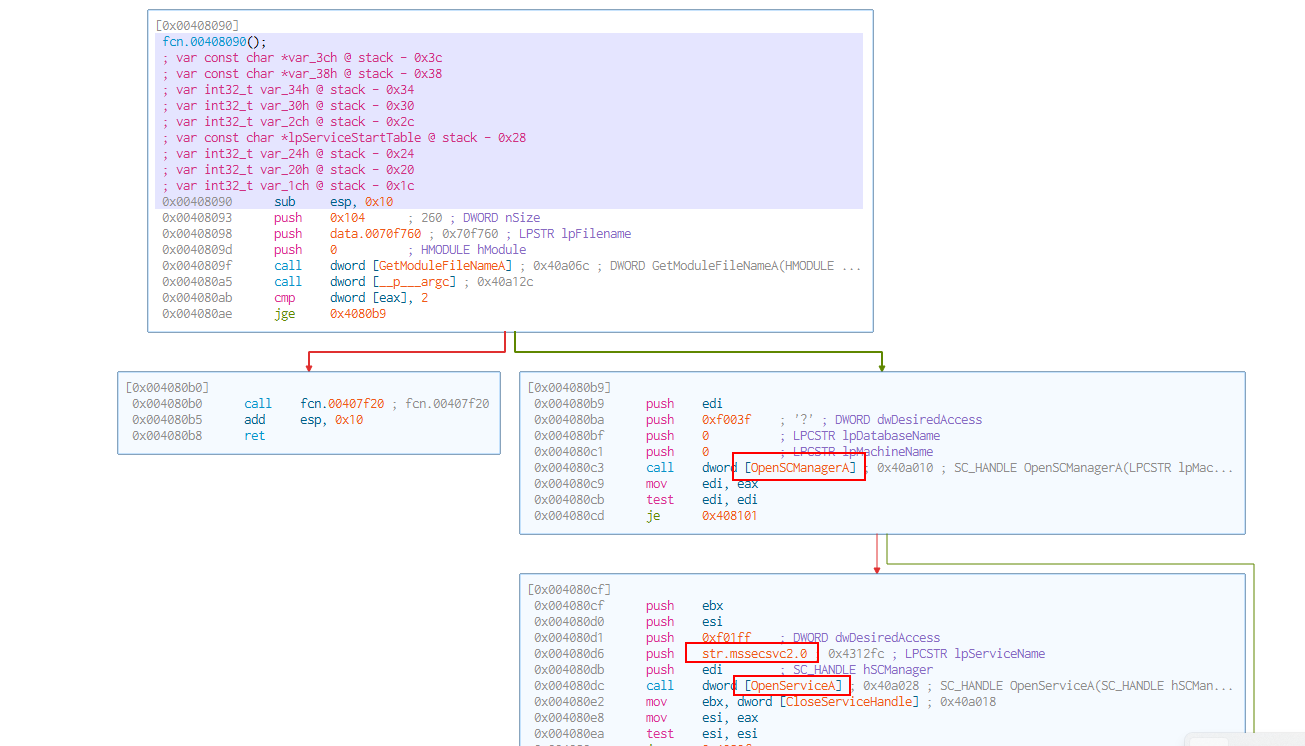
- Assuming that it got detonated it seems it is opening a service called “mssecsvc2.0” (if already exists) or taking the other path and creating it and starting it up.
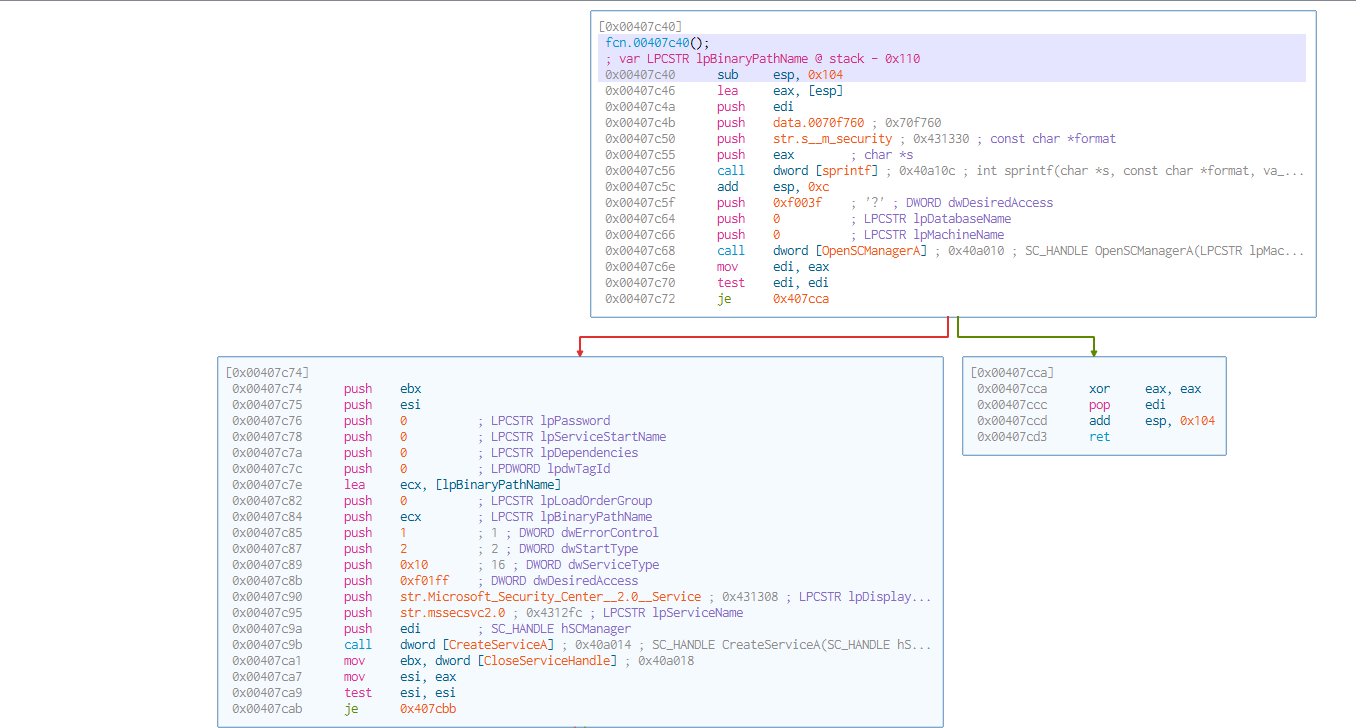
- I am going to stop here but I yet do not have the skills to go deeper into this rabbit hole!
Dynamic
Detonation Zero (Internet Connectivity)
- Absolutely nothing seems to have happened.
- At least I do not see anything out of order in my environment.
Detonation One (Internet Connectivity + Tools)
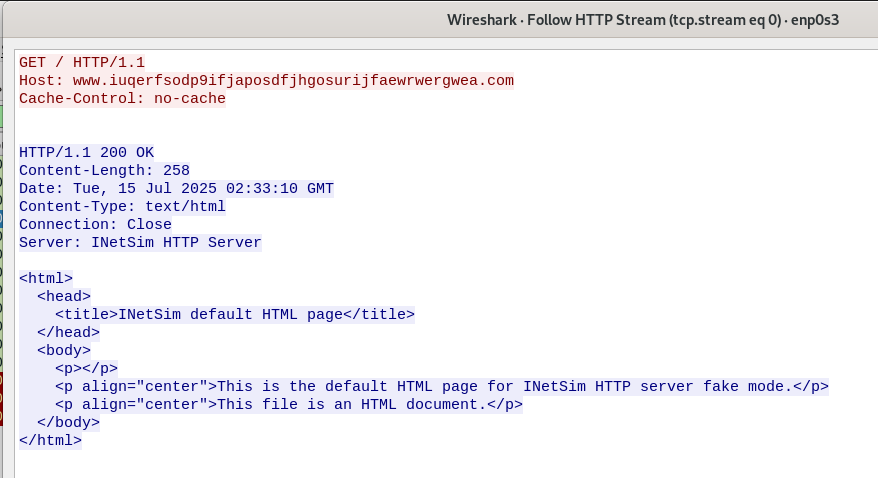
- WireShark:
- DNS query for “www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com”.
- HTTP request for “[hxxp]://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com”.
- The “server” (inetsim) responded with the HTML page.
- The client closed the connection with “RST” message.

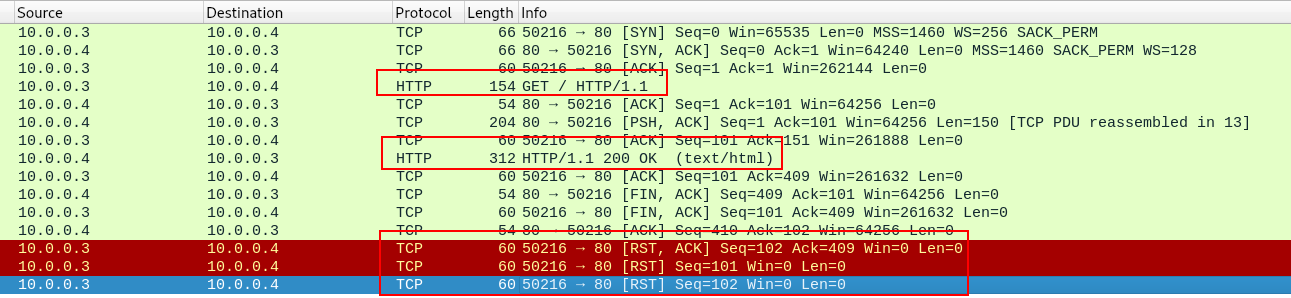
- PROCMON:
- We can see the the “Ransomware.wannacry.exe” is reading “wininet.dll”, then it opens a TCP Socket from port 50215 to port 80 and sends a message.
- This is what we saw from Wireshark.
- The “inetsim” replied, we can see this in the “TCP Receive” and then the “Ransomware.wannacry.exe” immediately disconnects.
- Sends the “RST” we saw in Wireshark.
- Immediately after this, we are exiting created threads because apparently there is nothing else to do.
- We can see the the “Ransomware.wannacry.exe” is reading “wininet.dll”, then it opens a TCP Socket from port 50215 to port 80 and sends a message.
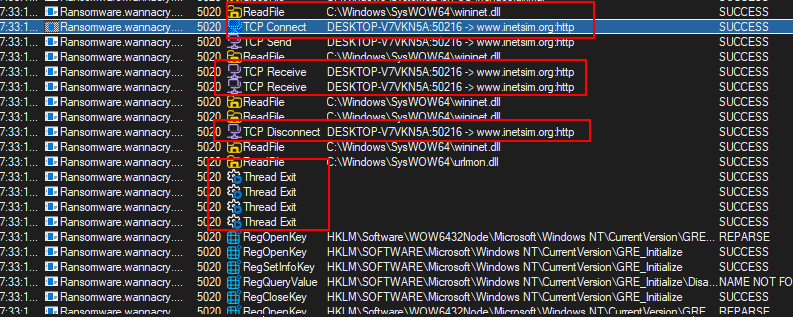
- Seems to be that the condition for this malware to detonate is to NOT being able to reach “[hxxp]://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com”.
- Matching our understanding of the malware in the static analysis.
Detonation Two (No Internet Connectivity)
- All my files, are slowly getting encrypted.
- A pop up appears for me to pay a ransom.
- Wallpaper changed.
- Executable “@WanaDecryptor@.exe” and file “@Please_Read_Me@.txt” got created.
- It seems to have the option to decrypt some of my files as “good faith”.




Detonation Three(No Internet Connectivity + Tools)
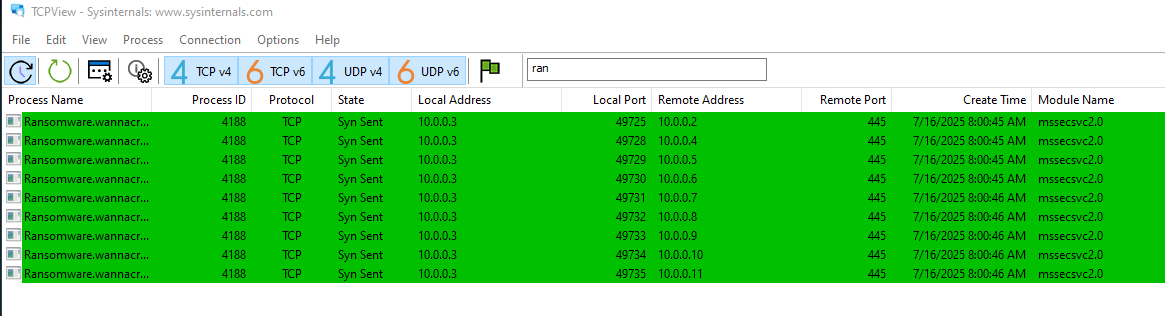
- Immediately after detonating we can see a bunch of connections to other IPs.
- Seems to be it is trying to enumerate IP’s in the subnet, establish a connection and spread the malware.
- Notice this is port 445. This is “EternalBlue” vulnerability, it was a vulnerability in Microsoft’s implementation of SMB.
- The focus of this article is not EternalBlue. Just notice the connections that it is trying to establish to propagate itself.
- Let’s follow the PROCMON process and try to identify the big moving parts here.
- This all starts by executing: ‘“C:\Users\flareuser\Desktop\Ransomware.wannacry.exe” ‘. This is given a PID of 548.
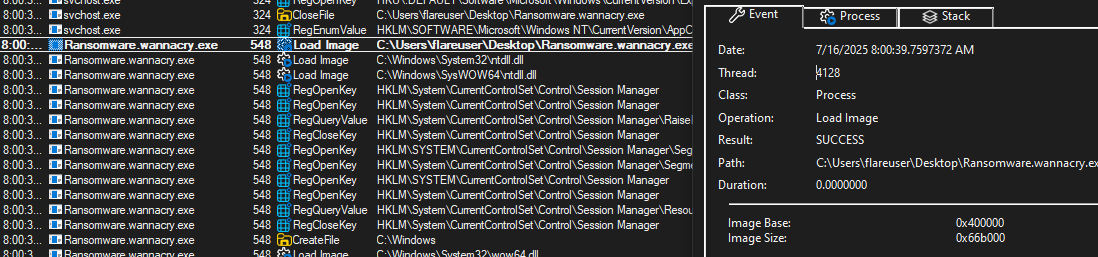
- “Ransomware.wannacry.exe” then creates a service called “mssecsvc2.0”.
- The way this works is that the executable calls CreateServiceA API and the one that ends up creating the service is “services.exe”.
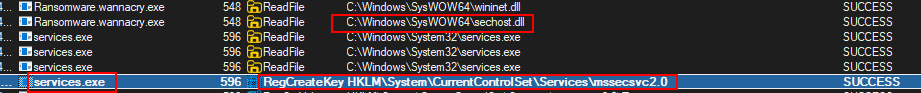
- When searching in the “services” window, we can see a “Microsoft Security Center (2.0)” called “mssecsvc2.0”.
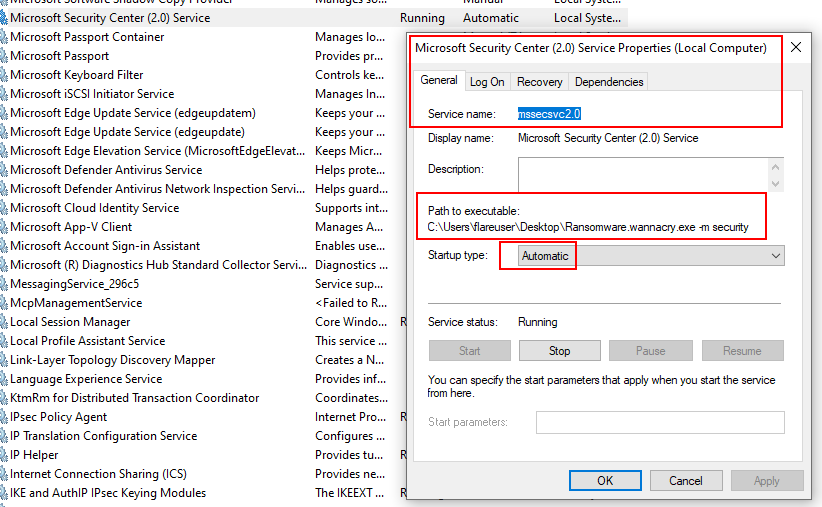
- Path to executable: ‘“C:\Users\flareuser\Desktop\Ransomware.wannacry.exe -m security”’.
- The status is running and it starts automatically.
- This is how the executable achieves persistence.
- Basically it runs the same executable but with “-m security” option.
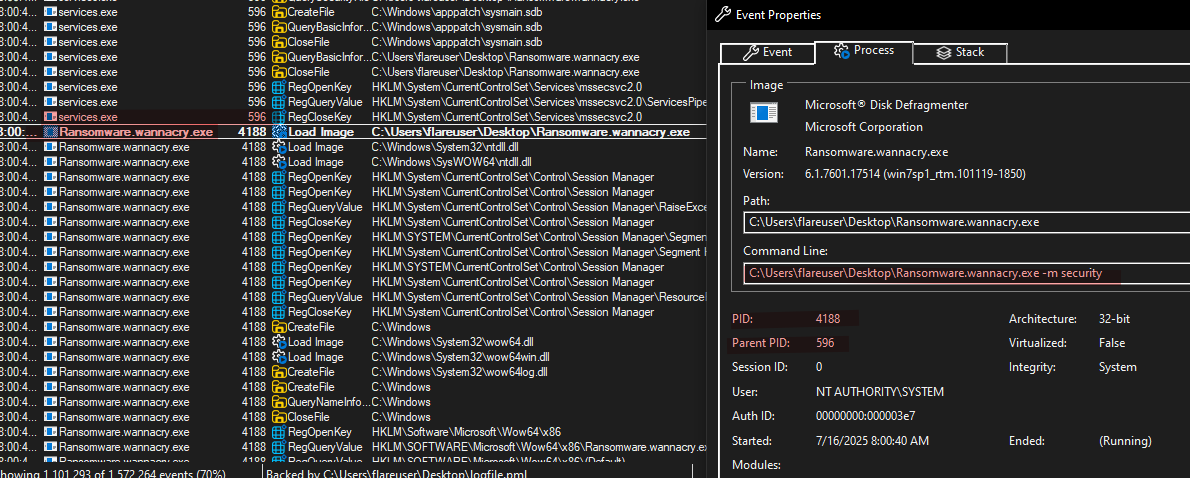
- Following the PROCMON we can now see service “mssecsvc2.0” started and therefore, executed ‘“C:\Users\flareuser\Desktop\Ransomware.wannacry.exe -m security”’.
- We know “services.exe” started this because the Parent PID of “Ransomware.wannacry.exe -m security” is 596, which is “services.exe”.
- Executing “Ransomware.wannacry.exe” with options “-m security” got a PID of 4188.
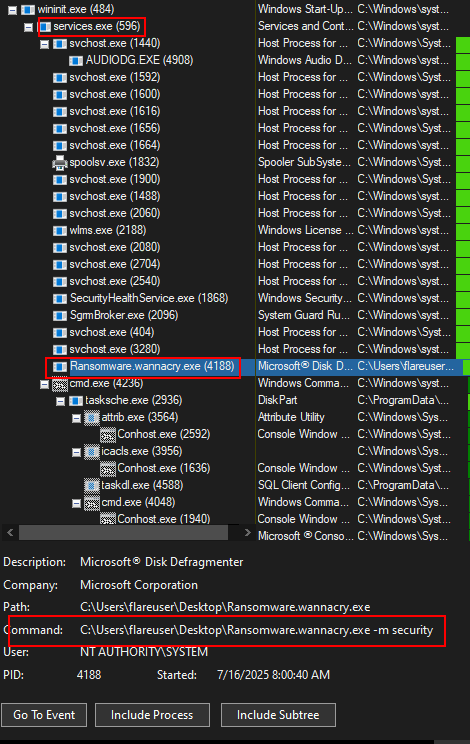
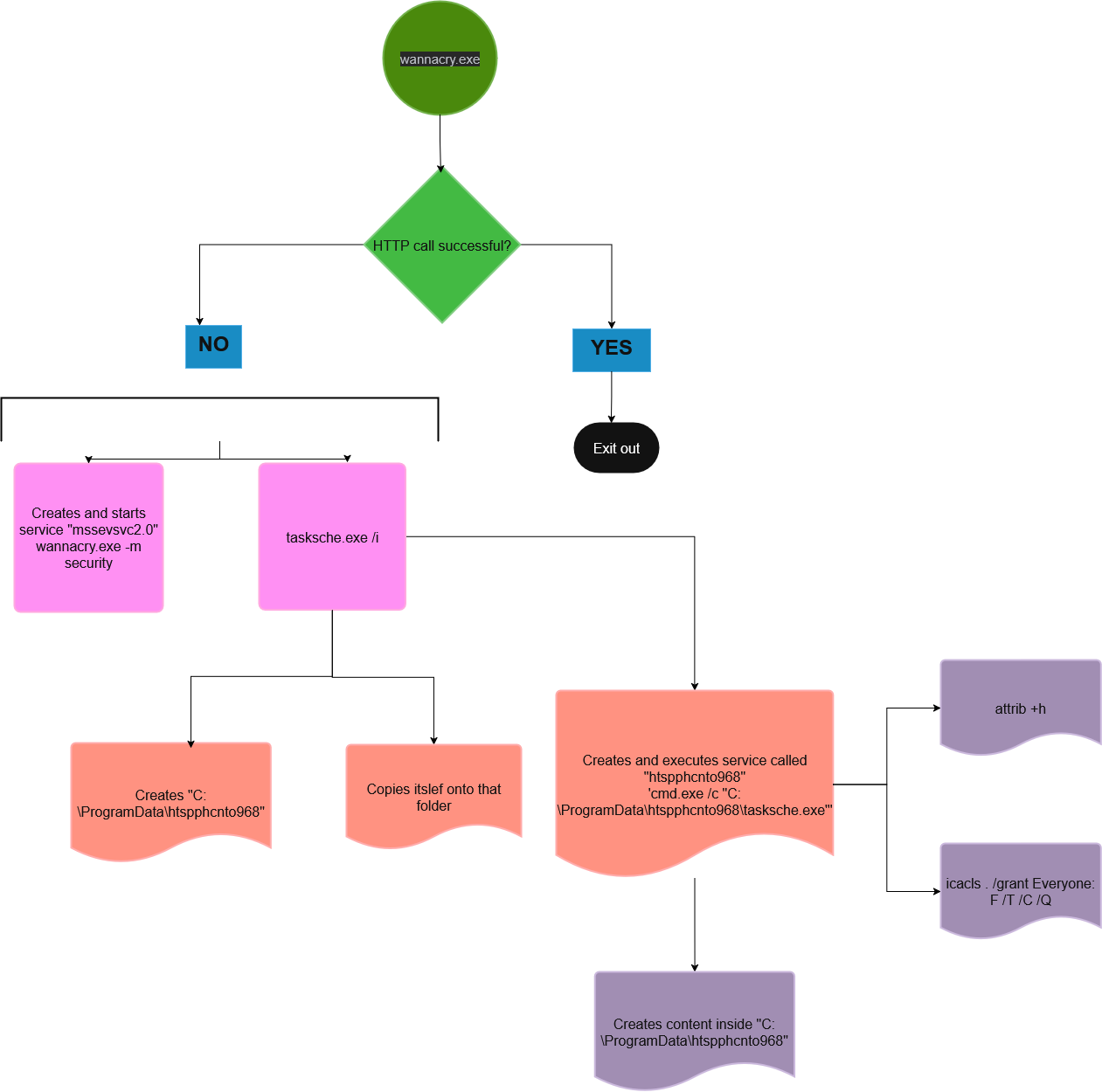
- Now PID 548 (remember this is the original detonation “Ransomware.wannacry.exe” with no options) starts “C:\WINDOWS\ tasksche.exe /i “ that received a PID of 4668.
- Again, the Parent PID of “tasksche.exe /i” is 548
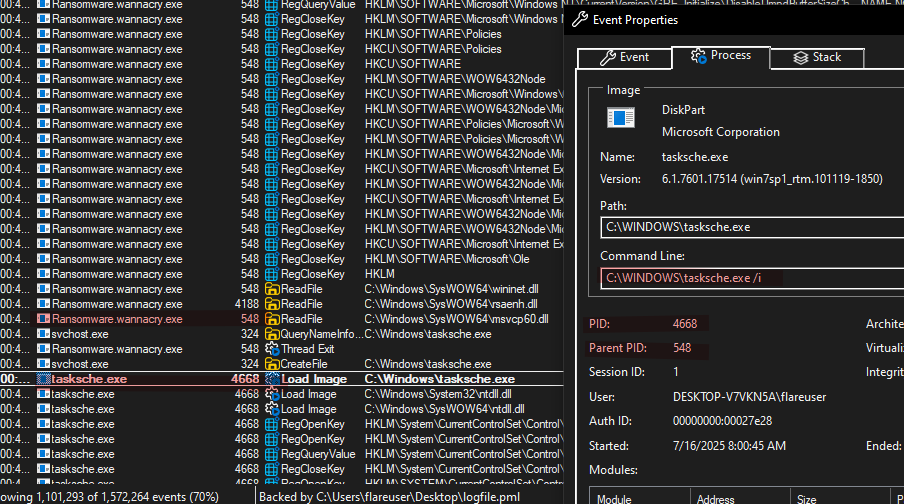
- Now the “C:\WINDOWS\tasksche.exe /i” proceeds and do several things:
- Creates folder “C:\ProgramData\htspphcnto968”.
- Copies itself inside that folder (“C:\ProgramData\htspphcnto968\tasksche.exe”).
- Creates a service called “htspphcnto968” (seems to be random characters).
- Again, this ends up being created by “services.exe”


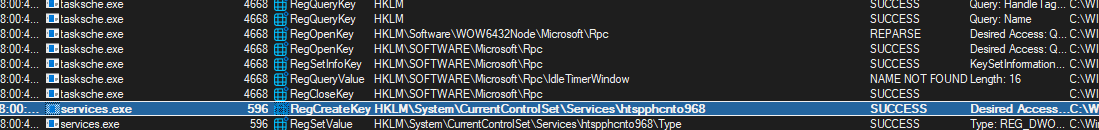
- Taking a look at service “htspphcnto968”:
- Path to executable: ‘cmd.exe /c “C:\ProgramData\htspphcnto968\tasksche.exe”’.
- Startup type: Automatic.
- Persistence
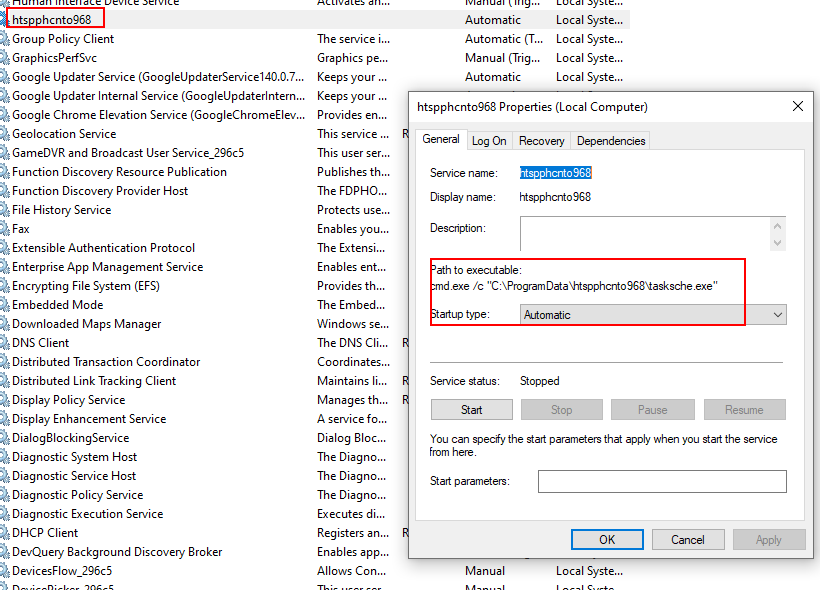
- This gets executed and now “C:\ProgramData\htspphcnto968\tasksche.exe” got a PID of 2936.
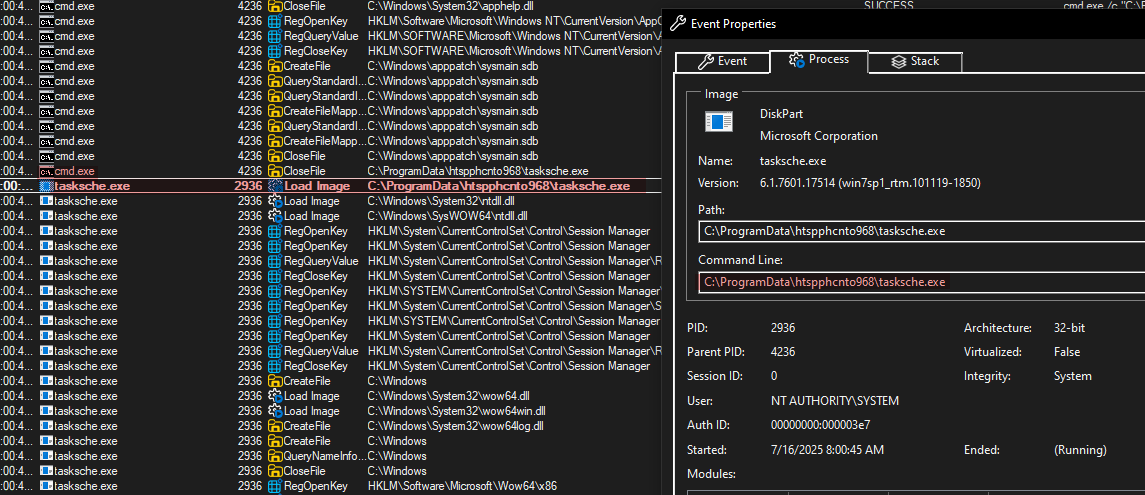
- PID 2936 seems to be in charge of populating/extracting/creating all the content inside “C:\ProgramData\htspphcnto968” directory.
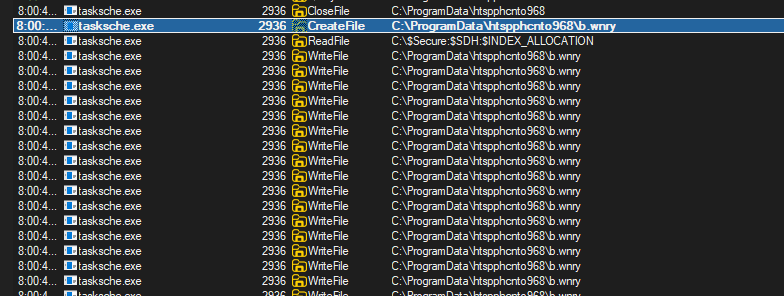
- Inside this folder I can only guess what might be here:
- Extracted binaries from main payload.
- Messages to display to the users in different languages.
- Keying material from encryption/decryption.
- Maybe some files contain another executable(?)

- PID 2936 spawns “attrib +h .” and “icacls . /grant Everyone:F /T /C /Q” to make folder “htspphcnto968” and grant full access to group “Everyone”.

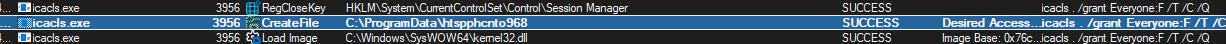
- There are other executables that I not sure what they do but they probably deal with the infection process and encryption/decryption process, payment,etc.
-
These feels like the big moving parts that I noticed in the “Ransomware.wannacry.exe” executable.
- Here is a table of reference for the PID’s and other details.
- Where “*” means we don’t care about that value.
- Where “-“ means there was no value provided.
| Process | Argument | PID | Parent PID |
|---|---|---|---|
| “\Desktop\Ransomware.wannacry.exe” | - | 548 | * |
| “services.exe” | - | 596 | * |
| “\Desktop\Ransomware.wannacry.exe” | -m security | 4188 | 596 |
| “C:\WINDOWS\tasksche.exe” | /i | 4668 | 548 |
| C:\ProgramData\htspphcnto968\tasksche.exe | - | 2936 | * |
| “attrib.exe” | +h | * | 2936 |
| “icacls” | /grant Everyone:F /T /C /Q | * | 2936 |
- If I were to create a flow of the process it would look something like this:
Answers
- Record any observed symptoms of infection from initial detonation. What are the main symptoms of a WannaCry infection?
- The wallpaper changed.
- Data got encrypted.
- A pop-up keeps appearing saying I need to pay a ransom.
- A “@Please_Read_Me@.txt” file.
- Use FLOSS and extract the strings from the main WannaCry binary. Are there any strings of interest?
- Mainly the string “[hxxp]://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com “
- Inspect the import address table for the main WannaCry binary. Are there any notable API imports?
- Yes there are. However, we cannot jump to any conclusion just yet.
- InternetOpenUrlA
- Sleep
- CryptGenRandom
- IsDebuggerPresent
- VirtualAlloc
- Yes there are. However, we cannot jump to any conclusion just yet.
- What conditions are necessary to get this sample to detonate?
- For this malware to detonate there must not be network connectivity. Specifically an HTTP request must not succeed to “[hxxp]://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com “
- Network Indicators: Identify the network indicators of this malware
- DNS request for domain name “www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com “
- HTTP call to “[hxxp]://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com”
- Many connections attempts to other hosts on the subnet over port 445.
- Host-based Indicators: Identify the host-based indicators of this malware.
- Data being encrypted.
- Wallpaper changed.
- Services “mssecsvc2.0” and “htspphcnto968” got created.
- A directory in “C:\ProgramData\htspphcnto968” got created.
- A “@WanaDecryptor.exe@” got created.
- Use Cutter to locate the killswitch mechanism in the decompiled code and explain how it functions.
- Image is in the static analysis section. Basically if “ZF” == 0 means the HTTP call was successful, then we jump and the program exits out. If “ZF” == 1 means HTTP call failed, then we execute the rest of the payload.